TL;DR:
Happy Veterans Day, especially to our resident pirate hunter, Hector. We celebrated by letting our Navy muscle lead an opsec training today.
On that note, this evening edition is brought to you by SIM hackers. I had my number ported AGAIN last week. This time, they hit my wife, too, so I’ll be cutting off their fingers if I ever find them. [Side note: I won’t because I’m not Liam Neeson, but the FBI might. If you’ve been the victim of a phone porting “SIM Swap”, reply to this email, and I can intro you to an agent working the case.]
Despite my prep, and a relatively fast recovery time, it was still a nightmare (again). How long are we gonna have to deal with this shitty security from the wireless cartel? What should you be doing to ward off phone porting.
Long Bitcoin, Short AT&T
You may have noticed we sent just three emails last week instead of five. That’s because for the second time in six months I was dealing with a phone porting hack.
If you don’t know what a “SIM Swap” is, read this.
In short, it’s where anyone, anywhere, for any reason can port your cell phone number to another service via a social engineering attack. It takes very little information about you or your account, and it will usually happen in the middle of the night. If you’re a public crypto person, a hacker probably has all they need to call up your carrier, ask to port your service, and do it successfully. (Sleep tight.)
Use your phone number as a recovery option for accounts like your email, or (please god no) your crypto wallets, and you’re gonna have a bad time.
That’s because AT&T representatives get judged based on customer service, not on whether they can prevent your doppelganger in Guatemala City from hijacking your service while the real you is mid-text from your home in NYC.
I’m not exaggerating. This is exactly what happened to me in May, despite the fact that I a) flagged my account as high-risk, b) added a pin, and c) demanded account changes only take place in store with a photo ID.
Back then, I was having cocktails during NYC Blockchain Week when my cell service suddenly conked out. Many wouldn’t think twice about losing service in a crowded bar, but as I’d just mixed it up earlier in the day with some #XRPthestandard winners, I thought, “could be a real hack this time.”
I went on opsec autopilot, sprinted down from the rooftop bar to snag wifi and lock down my accounts, and quickly learned they got my TBI twitter and work email, which still had SMS recovery options. (For the company email, I had 2fa secured with Authenticator, but had forgotten to remove my number as a recovery option. Tsk tsk. More on that later.)
After getting everything nice and secure (and calming down Hector, who I think was getting ready to waterboard suspects), I called my wife and parents, who’d both been woken up in the middle of the night with really charming, panic-inducing texts about how I was in trouble and needed money badly as an emergency bail out.
I assured them all that I was neither in trouble, nor in Guatemala City, and then proceeded to count down the hours until AT&T customer support would sign back online to fix the mess. (That’s right, it may be one half of a $400 billion duopoly, but they can’t afford a fucking 24 hour hotline.)
Whatever. I knew this might happen at some point.
Glass half-full, irrational id me goes to sleep thinking, “I’ve made it.” I then go to the AT&T store first thing in the morning, somehow manage to not take my frustration out on a very helpful field rep (but that was the problem initially, wasn’t it, AT&T?), and then run over to Brooklyn to give a keynote at Ethereal.
All accounts are secure, I’m back online, and there’s no real damage.
***
Fast forward to last week, in what was a much more sophisticated hack, that I hope scares the crap out of you to get your opsec in order.
Keep in mind, this is what happened to someone who has tried hard to keep things pretty tight AND already has battle scars from one attempted hack.
It was a long night grinding through the email backlog. I lucked out in that regard. At 1:15am, I notice my cell service go out. I’m working out of a little common area in our apartment building, that’s not at all ironically named a “cyber cafe”, so I quickly check all of my other email addresses to see if anyone’s trying to break in to my accounts. Yep. Lovely. Lock ‘em all down, and notify the Messari team and hosted crypto wallets.
Run back to the apartment and my wife asks, “are you doing something with our account? I got a message from AT&T and now the phones don’t work.” They got her phone, too.
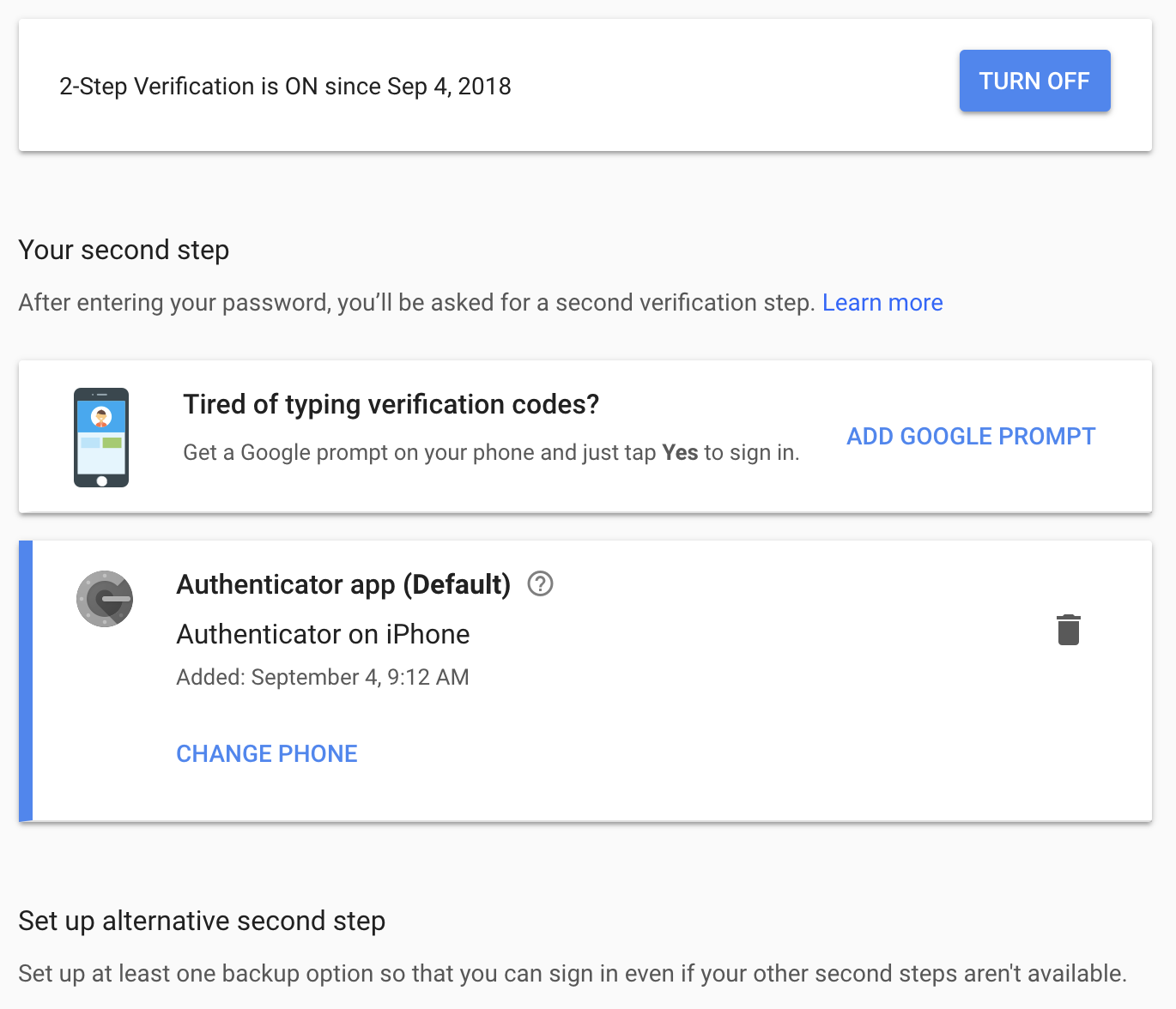
“Also, our internet is out.” That piques my interest. I run to her computer and see if she’s still signed in. Nope, they got her gmail. I notice her 2fa lists both Authenticator AND a cell number, very easy to overlook if you’re defaulting to the app. This is what 2fa should look like in gmail if you’ve set it up properly:
[Counterintuitively, you’ll have to set up a recovery phone with a number in order to activate Authenticator initially. Once that’s done, though, you need to go back and delete the SMS option. Easy to overlook.]
Wife’s gmail is connected to our cable service, so the hackers went in and knocked out our wifi to give themselves more time to work without interruption. If we hadn’t had the good ole cyber cafe, I’d have been in the dark that night and unable to secure anything. Scary for crypto suburbanites with homes. You better invest in a hotspot, and not rely on wifi in a pinch.
They tried to access most of my wallets, all of my email accounts (including some accounts I haven’t touched in years), iCloud, Dropbox, etc. Same for my wife’s accounts. Fortunately, they didn’t get into any of them.
I call AT&T customer service at 7am, they suspend the account. Then I go into the store at 10am, and again fail to yell at the friendly and very helpful reps.
I come home and start researching new cell providers. The only thing that holds me back (as in May) from switching to Project Fi (Google) from AT&T is the latter’s compatibility with iPhones.
I’m not going to rewrite a post on what exactly I’ll do now to beef things up, because I’ve already been targeted a couple of times, and sharing my playbook today seems dumb and like a challenge presented to the broader hacker ecosystem.
Fortunately, a couple people have already done good synopses for me.
If you’re losing sleep over this — which you should be if you have more than a few thousand followers, tweet about crypto, and don’t have proper 2fa and account recovery settings — here’s where you can start your opsec bootcamp:
Mason from Tokensoft on Minimum Viable Security
Panama Crypto on the Ten Commandments of Crypto Security
Lopp on a Modest Privacy Protection Proposal
Many in the industry have already lost millions.
Don’t be one of them.
-TBI
P.S. Stay safe out there, and help catch these scumbags by helping out the FBI. (Again, you can reply directly to this email for an intro.)
P.P.S. Share. Subscribe. Spread the (rational) crypto love. Tweet at me or Messari for requests, feedback, comments, or questions.
Best of the Rest - What We Missed Last Week
Every weekend, we dig through the past week’s posts from crypto’s other great sources of content to see what we missed in our own weekend reads.
Here’s us curating the curators:
DeFi vs Fintech- Tobia De Angelis
(h/t Token Economy)
Tobias writes a succinct explainer on why decentralized finance, or “DeFi”, is ontologically different from traditional financial technology services , or “Fintech”. For starters, Fintech is about building proprietary software, whereas DeFi’s focus is about building open source software. Additionally, there is no bureaucratic or technological gatekeeper between the builder and their idea in DeFi— and this is why builders are compounding towards DeFi. Even though DeFi still is a suboptimal choice on most dimensions for most of its use cases, Tobias argues that it’s wrong to compare Fintech and DeFi from the performance perspective because the focal point is not performance, but trust.
The Unintended Consequences of Product Design - Taylor Monahan
(h/t NLW)
Taylor’s musing are especially relevant now that UX and product design conversations are ramping up, and her experiences first with MyEtherWallet and now at MyCrypto highlight the sometimes vast difference between intentions and outcome. For example, the intention of making the user on boarding process easier can become so streamlined that it ceases to require users to save their private keys. Another example Taylor gives is the practice of saving private keys, or other secret information, to local storage in exchange for intended causes like ease to access, faster signup, account recovery options, etc. Takeaways? Do not underestimate the people using your product. That being said, people will always take the easiest path. In the end, focus on build a product that is safe and secure by default, and be mindful of attack vectors and always consider the best/worst case. TLDR: product design is hard.
Transaction count is an inferior measure - Nic Carter
In considering how to consistently compare dissimilar value-transfer systems like Bitcoin, Paypal, Visa, SWIFT, and physical cash, Nic urges to broadening the focus beyond simple transaction count— and mindful of the tradeoffs made by each system. There are at least three important variables to consider when holistically appraising a value transfer system, and the transaction rate is just one of them: Transaction capacity (tps), Typical transaction characteristics (transaction size), and Settlement assurance. Since value transfer systems vary along at least three major axes and not just one, the way to respond to TPS stats often requires a more holistic perspective.
Did I miss something?
Send me the link, your twitter handle and your best imitation compression algorithm write up. If I like it, I’ll include your bit next issue (with attribution).
Podcast Recap
🎧 ICYMI on the Messari podcast, Katherine breaks down the latest SEC order against EtherDelta’s founder, and what its implications are for DEX broadly (more in the Quick Bits as well). We also talk to Simon Taylor, founder of Global Digital Finance, about the importance of building a knowledge base and setting best practices for the crypto industry. (Ryan is an advisory board member, and Messari is a big supporter.) (17 min for your evening commute.)
Listen and subscribe to all of our podcasts— on Apple Podcasts here, Spotify here, and Google play here.
Some other great episodes are #12 (Erik Vorhees & Ari Paul at DevCon), #10 (Spencer Bogart on fund performance and tokenization), #9 (Tony Sheng on his writing process), #6 (Jake Chervinsky’s primer on federal & state crypto regulators), #4 (Nic Carter on data integrity in crypto), and #8 (Conversations on the ground at CryptoSprings).
Find our podcast series on Apple here, Google Play here, and Spotify here.
Shameless Plugs
We want your feedback!
We know Messari can feel like a couple different products right now, and we're working to unify our features into one overarching whole. To that end, We’ve made a Trello board to take in any and all of the feedback you have for us! Have at it 🛠
We're Hiring:
We need data engineers who want to bring transparency to crypto!
Join a fast growing team in NYC; work with crypto OGs, and former Bloomberg/Palantir engineers; & access a network that sets you up for the rest of your career. Apply here!
Upcoming Travel:
Hit us up in these locations:
Consensus Invest, New York, New York | November 28
Join Our Community:
If you are interested in helping us crowdsource token project details, or want to join our community to share your expertise, we’d love to have you on board! Take a second to fill out an application and we will get back to you soon.
Going forward, we’ll be capping new members at 15 each week to keep things running smoothly. If you haven’t heard back, you are probably in the queue.
Like what you read? Share it! Hate what you read? Let me know @MessariCrypto.